
Pakhnyushchyy - Fotolia
How security, compliance standards prevent OSI layer vulnerabilities
Each layer of the Open Systems Interconnection presents unique -- but connected -- vulnerabilities. Here's how to establish OSI security and compliance best practices.
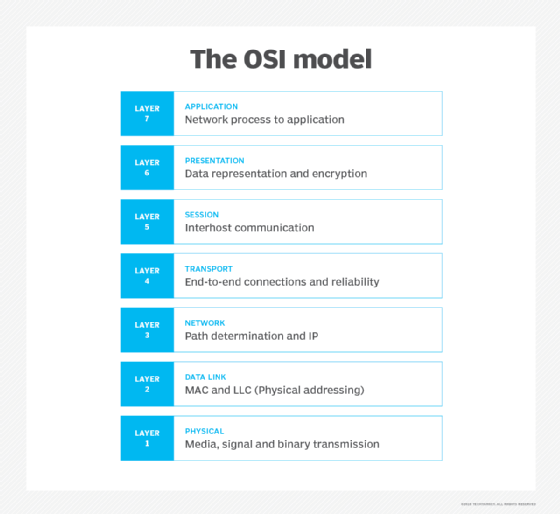
The Open Systems Interconnection -- or OSI model layers -- explains the process of endpoint communication via networking, and it is divided into seven different layers based on their functionality.
Every layer in the OSI model architecture relies on the layer above and on the layer below. If the lower layer does not function correctly, the next layer will fail to be properly executed and the entire process will be stopped.
The data is sent upward from the first layer of the source computer across the network and then flows downward through the layers within the receiving computer.
The OSI model was originally established to standardize the governance and compliance of transmission data packets and was adopted by the International Organization of Standardization (ISO) as a common reference. It is of particular importance for cybersecurity personnel to understand the OSI model, because hackers can easily pivot from layer to layer when exploiting computing system vulnerabilities such as distributed denial-of-service (DDoS) attacks that almost always target OSI layer vulnerabilities.
To establish the best network cybersecurity, organizations should focus on creating an OSI security and compliance framework for each of the seven layers of the OSI model, addressing vulnerabilities by layer and developing strategies to offset these risks.
Layer 1: The Physical layer
This is the bottom layer of the OSI model. Its focus is the transmission and reception of the unstructured raw bit stream over a physical medium. The physical layer covers a variety of devices and mediums, among them are cabling, connectors, receivers, transceivers and repeaters.
OSI layer vulnerabilities:
- Physical destruction, obstruction, manipulation or malfunction of physical assets including loss of power, loss of environmental control, theft of data and hardware.
- Physical damage or destruction of data and hardware.
- Unauthorized changes to the functional environment (data connections, removable media, adding/removing resources).
- Disconnection of physical data links; and undetectable interception of data, keystroke and other input logging.
OSI security and compliance strategies
Practice defense-in-depth tactics, incorporate access controls, accountability and auditing to track and control physical assets. Arrange cables to not allow eavesdropping and restrict access to the telecommunications room to protect sensitive equipment. Additionally, shut down open wall ports and use a managed power UPS.
Layer 2: The Data Link layer
This is a protocol layer that transfers the data frame in between nodes of the physical layer. Its responsibility is to conduct an error-free transfer, which allows the layer above it to assume they are error-free. The layer comprises two sub-layers: The logical link control layer and the media access control (MAC) layer.
OSI layer vulnerabilities:
- MAC address spoofing (station claims the identity of another) virtual LAN, or VLAN, circumvention (station may force direct communication with other stations, bypassing logical controls such as subnets and firewalls).
- Spanning Tree errors also may be accidentally or purposefully introduced, causing the Layer 2 environment to transmit packets in infinite loops.
- In wireless media situations, Layer 2 protocols may allow free connection to the network by unauthorized entities, or weak authentication and encryption may allow a false sense of security.
- Switches may be forced to flood traffic to all VLAN ports rather than selectively forwarding to the appropriate ports, allowing interception of data by any device connected to a VLAN.
OSI security and compliance strategies
Advance switches can be configured to limit the number of MAC addresses, which can be learned on ports connected to end stations. Use private VLANS and static Address Resolution Protocol entries.
Layer 3: The Network layer
This layer handles the routing of data and is also responsible for switching information from one network to another. This layer specifies the right destination for all transmission data at the packet level. IP is the most common example of a network layer operating on the internet.
OSI layer vulnerabilities:
- Route spoofing, or propagation of false network topology, IP address spoofing, where false source addressing on malicious packets, Identity & Resource ID Vulnerability.
- Reliance on addressing to identify resources and peers can be too rigid and vulnerable.
- ICMP flooding -- a Layer 3 infrastructure DDoS attack method that uses Internet Control Message Protocol messages to overload the targeted network's bandwidth.
OSI security and compliance strategies
Prevention of attacks is done by rate-limiting ICMP traffic and correctly configuring ACLs, or Access Control Lists. This allows or refuses connections with equipment belonging to other networks. Implementing IPsec: the suite of protocols responsible for providing security features land activating firewalls on this layer.
Check out part two of this tip to learn compliance strategies to prevent vulnerabilities in OSI Layers 4 through 7.







