Ensure IAM compliance by wielding key controls and resources
IAM compliance is a top priority for CIOs. Read up on IAM standards and regulations, and learn how to implement IAM controls to best stay compliant.
If an IT organization survives a compliance audit, this implies that its identity and access management program is in good shape -- especially if it is an IT general controls audit. The company is likely also in compliance with the majority of standards and regulations that address IAM.
IAM compliance is often among the top three items on a CIO's priority list. It is important to examine how IAM compliance fits into an organization's overall compliance strategy. In this article, get guidance on the relevant IAM compliance regulations and standards, as well as suggestions to help achieve compliance with them.
IAM components relevant to compliance
The first step toward achieving and maintaining IAM compliance is to understand each of the elements of IAM that are relevant to the organization's compliance goals. These components of IAM must be incorporated into the overall compliance program to ensure confidentiality, integrity, availability and privacy of information. The table below lists items to address from audit and compliance perspectives.
The controls are usually included in IAM standards and regulations to varying degrees. They are also included among IT general controls that are used to perform general IT audits.
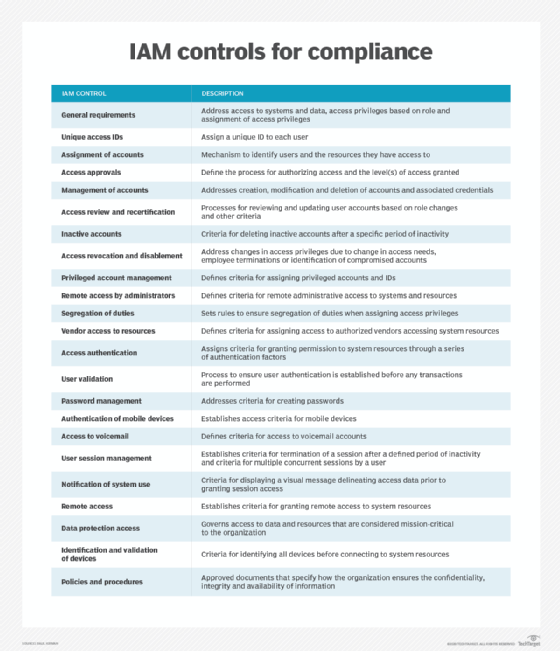
IAM compliance standards, regulations and guidance
Multiple organizations have established standards, regulations and other criteria for ensuring IAM programs are provided by public and private sector entities.
Ongoing proactive management of IAM controls and related activities, supplemented by periodic audits and reviews, can confirm an organization's compliance with these critical requirements, including the following:
- COBIT. Originally developed by ISACA, COBIT requirements are specifically designed for IT departments in any kind of organization.
- ISACA. In addition to COBIT, ISACA also provides a variety of audit and compliance documents users can refer to when examining IAM controls prior to an audit.
- U.S. Federal Financial Institutions Examination Council (FFIEC). Providing compliance standards for financial institutions, FFIEC has both an information security (infosec) workbook and audit guidelines that address IAM requirements.
- Sarbanes-Oxley Act. Section 404 of this U.S. legislation specifies controls for preparing financial reports and ensuring the integrity of report data.
- Gramm-Leach-Bliley Act. The U.S. federal law requires financial institutions to have controls that protect the confidentiality of nonpublic customer data.
- HIPAA. The U.S. federal law's Security Rule and Privacy Rule define controls that address the security and privacy of protected health information, among other issues.
- Family Educational Rights and Privacy Act. This law mandates that U.S. educational institutions must provide controls to protect student records and associated data.
- North American Electric Reliability Corporation. This organization provides standards and controls for protecting information as used by electric power utilities.
- NIST. NIST Special Publication 800-63-3 Digital Identity Guidelines and its three companion standards -- SP 800-63A, B and C -- address IAM requirements for federal agencies. NIST SP 800-53 addresses infosec requirements for federal information systems and organizations.
- International Organization for Standardization (ISO). The ISO 27000 series of standards addresses IAM requirements, which are widely used as an audit benchmark.
- PCI DSS. This global security standard addresses IAM issues for payment card distributors.
- GDPR. This European standard addresses a broad range of data security and protection issues, including IAM requirements.




