How to create an incident response playbook
Using an incident response playbook can speed up an organization's responses to cyberattacks. Find out how to build repeatable playbooks to use for different types of incidents.
Creating and maintaining an incident response playbook can significantly improve the speed and effectiveness of your organization's incident response. Even better, you can usually build a playbook without a lot of extra time and effort.
To help, here's a crash course on what incident response playbooks are, why they are important, how to use them and how to build them.
What is an incident response playbook?
An incident response playbook defines common processes or step-by-step procedures needed for your organization's incident response efforts in an easy-to-use format. Playbooks are designed to be actionable, meaning they quickly tell incident response team members what actions they need to perform under different circumstances. For example, a playbook might have plays for formally declaring an incident, collecting and safeguarding digital evidence, eradicating ransomware or other malware from an environment and coordinating a data breach announcement with the PR team, as well as many other steps.
Why are incident response playbooks important?
Every minute counts in incident response. A playbook provides a single, authoritative, up-to-date source of instructions for all personnel with incident response roles and responsibilities. Everyone should know where to find the latest information at all times.
The benefits of adopting playbooks for incident response include the following:
- Incident response activities are consistent throughout the organization, and staff are less likely to skip steps within processes and procedures.
- Responses should start sooner and be performed more quickly with a playbook to follow. This reduces the length of incidents and the damage they could cause. Your organization's normal operations should also resume faster.
- The playbook effectively provides a common language all incident response personnel can speak. You can save time and improve results by pointing someone to a particular play rather than trying to quickly explain what you'd like them to do, for example.
Types of incident response playbooks
Security incidents occur in many ways. It's impossible for organizations to develop step-by-step instructions for each because they require different responses.
To help with the task, NIST provides broad groupings of incidents based on common attack vectors that can be used as a basis for defining specific handling procedures. Some common attack vectors to identify and create playbooks for include the following:
- External or removable media attacks from peripheral devices, flash drives or CDs.
- Attrition attacks that use brute-force methods to compromise or destroy systems, networks or services.
- Website or web-based attacks.
- Email-based and social engineering attacks -- for example, phishing.
- Acceptable use policy violations by an authorized user that result in an attack. This could include malicious or negligent insider threats.
- The loss or theft of equipment such as a company-issued smartphone or laptop.
How can you use an incident response playbook?
Incident response playbooks aren't just valuable for responding to actual incidents; they typically have other uses. For example, playbooks are great assets to get new staff up to speed on how your organization conducts incident response activities. They're also highly useful for incident response exercises and tests. In an incident response tabletop exercise, participants can reference particular plays to indicate how they would act in a real situation. In a test, participants' actions can be compared to what the playbook specified.
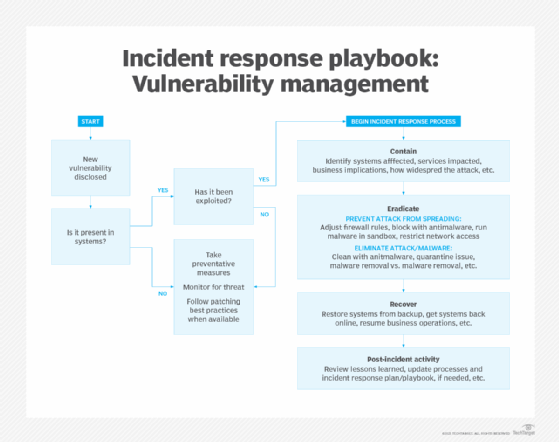
How to build an incident response playbook
The following key steps go into building an effective incident response playbook that works well for your organization:
- Consider using existing playbooks and frameworks. Review publicly available incident response playbooks to see which activities they document, how much detail they provide on each activity and how they organize the sets of activities. Many organizations opt to use playbooks that follow the phases of the NIST incident response framework: preparation, detection and analysis, containment, eradication and recovery, and post-incident activity.
- Assess and update existing incident response programs. Gather your existing policies, procedures and other documentation related to incident response activities. Assess them for completeness, accuracy and usability.
- Write well-organized playbooks. Properly plan the contents of your playbook, as well as how they should be structured and organized. This is a balancing act. The more detailed the plays are -- and the more comprehensive the playbook is -- the more effort it takes to create and maintain. But the effort could save time for your incident responders. One method for building a playbook is to list all potential response actions to a particular incident, as well as their correlating processes and procedures.
- Make playbooks user-friendly. Ensure incident response playbooks are easy to read and use. Once your organization's specific playbook needs are identified, write up simple steps for users to follow. If steps are unclear or complicated, team members could struggle to complete their necessary tasks during an incident and delay response times.
- Update playbooks and plans if necessary. Conduct post-incident analysis and feedback to review how well a playbook worked against a real and unscripted incident. Gather feedback from everyone who used the playbook to determine how well it informed them of the various steps to take and if anything proved confusing or unwieldy. Once feedback is collected, review it against the existing playbooks and make changes or updates, as needed.
As you build your playbooks, be sure to get feedback from the people who will be using the playbook. If your playbook is hard to use, it could be more of a hindrance than a help, so their input on plays and playbook drafts is invaluable.
Karen Scarfone is the principal consultant at Scarfone Cybersecurity in Clifton, Va. She provides cybersecurity publication consulting to organizations and was formerly a senior computer scientist for NIST.







