How to develop a cybersecurity strategy: Step-by-step guide
A cybersecurity strategy isn't meant to be perfect, but it must be proactive, effective, actively supported and evolving. Here are the four steps required to get there.
A cybersecurity strategy is a high-level plan for how your organization will secure its assets during the next three to five years. Obviously, because technology and cyber threats can both change unpredictably, you'll almost certainly have to update your strategy sooner than three years from now. A cybersecurity strategy isn't meant to be perfect; it's a strongly educated guess as to what you should do. Your strategy should evolve as your organization and the world around you evolve.
The intended outcome of developing and implementing a cybersecurity strategy is that your assets are better secured. This generally involves a shift from a reactive to a proactive security approach, where you're more focused on preventing cyber attacks and incidents than reacting to them after the fact. But solid cybersecurity strategies will also better prepare organizations to respond to those incidents that do occur. By preventing minor incidents from becoming major ones, organizations can preserve their reputations and reduce harm to employees, customers, stockholders, partners and other interested parties.
How do you build a cybersecurity strategy for your business?
Building a cybersecurity strategy for your business takes effort, but it could mean the difference between surpassing your competitors and going out of business. Here are the basic steps to follow in developing an effective security strategy.
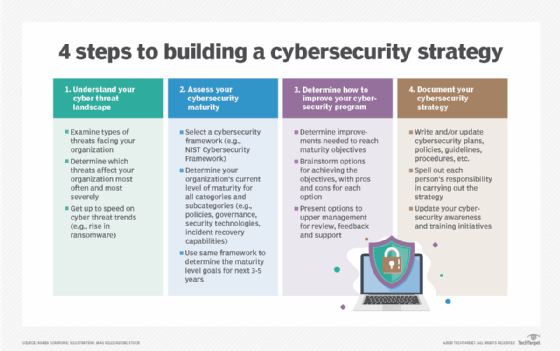
Step 1. Understand your cyber threat landscape
Before you can understand your cyber threat landscape, you need to examine the types of cyber attacks that your organization faces today. Which types of cyber threats currently affect your organization the most often and most severely: ransomware, other forms of malware, phishing, insider threats or something else? Have your competitors had major incidents recently, and if so, what types of threats caused them?
Next, get yourself up to speed with predicted cyber threat trends that could affect your organization. For example, many security researchers feel that ransomware is going to become an even bigger threat as ransomware gangs flourish and expand their attacks. There's also increasing concern about supply chain vulnerabilities caused by, for example, purchasing compromised components and either using them within your organization or building them into products you sell to customers. Understanding what cybersecurity threats you'll face in the future and the likely severity of each of them is key to building an effective cybersecurity strategy.
Step 2. Assess your cybersecurity maturity
Once you know what you're up against, you need to do an honest assessment of your organization's cybersecurity maturity. Select a cybersecurity framework, like the NIST Cybersecurity Framework developed by the National Institute of Standards and Technology. Use it first to assess how mature your organization is in dozens of different categories and subcategories, from policies and governance to security technologies and incident recovery capabilities. This assessment should include all of your technologies, from traditional IT to operational technology, IoT and cyber-physical systems.
Next, use the same cybersecurity framework to determine where your organization should be in the next three to five years in terms of maturity for each of those categories and subcategories. For example, if distributed denial-of-service attacks will be a major threat, you may want your network security capabilities to be particularly mature. If ransomware will be your biggest security issue, ensuring that your backup and recovery capabilities are highly mature may be key. If the remote work policies that were driven by COVID-19 have or will become permanent at your company, temporary tools deployed during the pandemic need to be hardened. The maturity levels you're targeting are your new strategic objectives.
Step 3. Determine how to improve your cybersecurity program
Now that you've established a baseline and determined where you want to be going forward, you need to figure out the cybersecurity tools and cybersecurity capabilities that will help you reach your destination. In this step, you determine how to improve your cybersecurity program so that you achieve the strategic objectives you've defined. Every improvement will consume resources -- money, staff time, etc. You'll need to think about different options for achieving the objectives and the pros and cons of each option. It may be that you decide to outsource some or all of your security tasks.
Cybersecurity career advice
Looking to further your career in cybersecurity? These four articles provide timely information on how to build the technical and personal skills you'll need to be successful.
Cybersecurity career path: 5-step guide to success
10 cybersecurity certifications to boost your career
When you've selected a set of options, you'll want to present them to upper management at your organization for their review, feedback and -- hopefully -- support. Changing the cybersecurity program may affect how business is done, and executives need to understand that and accept it as being necessary in order to sufficiently safeguard the enterprise from cyber threats. Upper management may also be aware of other plans for the coming years that your efforts could take advantage of.
Step 4. Document your cybersecurity strategy
Once you have management approval, you need to ensure your cybersecurity strategy is documented thoroughly. This includes writing or updating risk assessments, as well as cybersecurity plans, policies, guidelines, procedures and anything else you need to define what's required or recommended in order to achieve the strategic objectives. Making it clear what each person's responsibilities are is key.
Be sure that, as you're writing and updating these documents, you're getting active participation and feedback from the people who will be doing the associated work. You also need to take the time to explain to them why these changes are being made and how important the changes are so that, hopefully, people will be more accepting and supportive of them.
And don't forget that your cybersecurity strategy also necessitates updating your cybersecurity awareness and training efforts. Everyone in the organization has a role to play in mitigating security issues and improving your enterprise cybersecurity program. As your risk profile changes, so must your cybersecurity culture.
Monitor and reassess security threats and strategy
Developing and implementing a cybersecurity strategy is an ongoing process and will present many challenges. It's critically important that you monitor and reassess your organization's cybersecurity maturity periodically to measure the progress you're making -- or not making -- toward your objectives. The sooner you identify an area that's falling behind, the sooner you can address it and catch up. Measuring progress should include internal and external security audits plus tests and exercises that simulate what would happen under different circumstances, like a major ransomware incident.
Finally, be prepared to rethink your cybersecurity strategy if a major new threat arises. Agility in security is increasingly important. Don't be afraid to update your strategy as cyber threats and security technologies change and as your organization acquires new types of assets that need safeguarding.







