OPSEC (operations security)
What is OPSEC?
OPSEC (operations security) is a security and risk management process and strategy that classifies information, then determines what is required to protect sensitive information and prevent it from getting into the wrong hands.
OPSEC gets information technology (IT) and security managers to view their operations and systems as potential attackers would. OPSEC includes analytical activities and processes, such as social media monitoring, behavior monitoring and security best practices.
OPSEC was developed as a methodology during the Vietnam War when U.S. Navy Admiral Ulysses S. Grant Sharp, commander in chief of the U.S. Pacific Command, established the Purple Dragon team to find out how the enemy obtained information on military operations before those operations took place.
As a military term, OPSEC described strategies to prevent adversaries or potential adversaries from discovering critical operations-related data. This concept has spread from the military to other parts of the federal government, including the Department of Defense (DOD), to protect national security.
As information management and protection have become important to success in the private sector, OPSEC measures are now common in business operations.
What are the 5 steps in OPSEC?
The processes that make up operations security come down to these five steps:
1. Identify critical information. The first step is to determine what data would be particularly harmful to the organization if an adversary obtained it. This includes intellectual property, employees' or customers' personally identifiable information, financial statements, credit card data and product research.
2. Analyze threats. The next step is to identify who is a threat to the organization's critical information. There may be numerous adversaries who target different information, and companies must consider any competitors or hackers who might target the data.
3. Analyze vulnerabilities. In the vulnerability analysis stage, the organization examines potential weaknesses among the safeguards in place to protect critical information and identifies which ones leave it vulnerable. This step includes finding any potential lapses in physical and electronic processes designed to protect against the predetermined threats or areas where a lack of security awareness training leaves information open to attack.
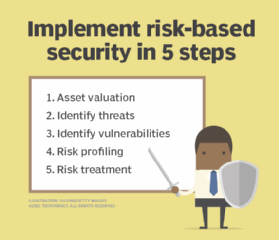
4. Assess risks. The next step is to determine the threat level associated with each of the identified vulnerabilities. Companies rank the risks according to factors such as the chances a specific attack will occur and how damaging such an attack would be to operations. The higher the risk, the more pressing is the need to implement risk management
5. Apply appropriate countermeasures. The last step involves deploying an OPSEC plan that will reduce the risks. The best place to start is with the risks that are the biggest threat to operations. Potential security improvements include implementing additional hardware and training and developing new information governance
Operations security best practices
Organizations developing and implementing an end-to-end operations security program will want to follow these best practices:
- Change-management processes. Companies must put change-management processes in place for employees to follow when adjustments are made to the network.
- Restrict device access. Organizations should only allow devices to access their networks that absolutely must have that access, and they should use network device authentication.
- Implement least-privileged access. Businesses must assign employees the minimum level of access to networks, data and resources they need to successfully perform their jobs. The principle of least privilege ensures systems, applications, processes or users have only the minimum access they need to do their job or function.
- Deploy dual control. Companies must ensure the teams and individuals responsible for maintaining the corporate network are separate from the teams and individuals responsible for setting security policies. This approach guards against conflicts of interest and other issues.
- Implement automation. People are typically the weakest links when it comes to enterprise security. Humans make errors -- inadvertently or on purpose -- causing data to end up in the wrong hands, overlooking or forgetting important details, and bypassing critical processes. Automation can eliminate these errors.
- Craft a disaster recovery plan. A key part of any information security defense is to plan for disaster and implement a strong incident response plan. Even the most fully functional OPSEC program must be accompanied by disaster plans identifying risks and detailing how a company will respond to cyberattacks and limit potential damages.
OPSEC and risk management
OPSEC encourages managers to view operations and projects from the outside-in -- that is, from the perspective of competitors or enemies in order to identify weaknesses. If an organization can easily extract its own information while acting as an outsider, the odds are outside adversaries can as well. Completing regular risk assessments is key to identifying vulnerabilities.
Risk management encompasses the ability to identify vulnerabilities and threats before they turn into real issues. OPSEC forces managers to do in-depth analyses into their operations and determine where sensitive data can be easily breached. By looking at operations from a bad actor's perspective, managers can spot vulnerabilities they might have missed and they can implement the right OPSEC processes to protect sensitive information.
OPSEC training
The Center for Development of Security Excellence (CDSE) is part of the DOD's Defense Counterintelligence and Security Agency offers security training for military personnel and DOD employees and contractors. The group uses web-based e-learning formats to present its training programs.
Areas covered in CDSE training include:
- define operations security;
- identify critical information;
- know OPSEC's five steps;
- recognize potential threats and how they might lead an adversary to uncover sensitive information; and
- apply appropriate countermeasures to protect critical data.
Occasional users of CDSE courses are taking them on the Security Awareness Hub website where students do not have to register. After the course, participants receive a certificate of completion. However, CDSE does not keep records of who completes the course.
CDSE training is also available through its Security, Training, Education and Professionalization Portal, a learning management system portal for all of the organization's security courses. Students taking CDSE courses regularly use the portal, which tracks completion. It also provides a transcript that can then be used to request American Council on Education and continuing education credits.
OPSEC strategies and processes are interrelated with the work of SecOps teams. Find out more about the role of SecOps and the security operations center in the enterprise.







